Time Matters: A Step-by-Step Guide to Updating Your Time Zone in Webmail
Introduction “Welcome! In this quick guide, we’ll walk you through the steps to change your time zone settings in your webmail account. Adjusting your time zone ensures that your emails display the correct timestamps according to your current location. Whether you’ve relocated or simply need to synchronize your email activity with your local time, this […]
Step-by-Step Guide: Installing WordPress Using Softaculous in Minutes
Introduction: Installing WordPress using Softaculous is a straightforward process that allows users to quickly set up their website or blog without the need for extensive technical knowledge. Softaculous is a popular auto-installer available in many web hosting control panels, making it easy for users to deploy WordPress with just a few clicks. In this guide, […]
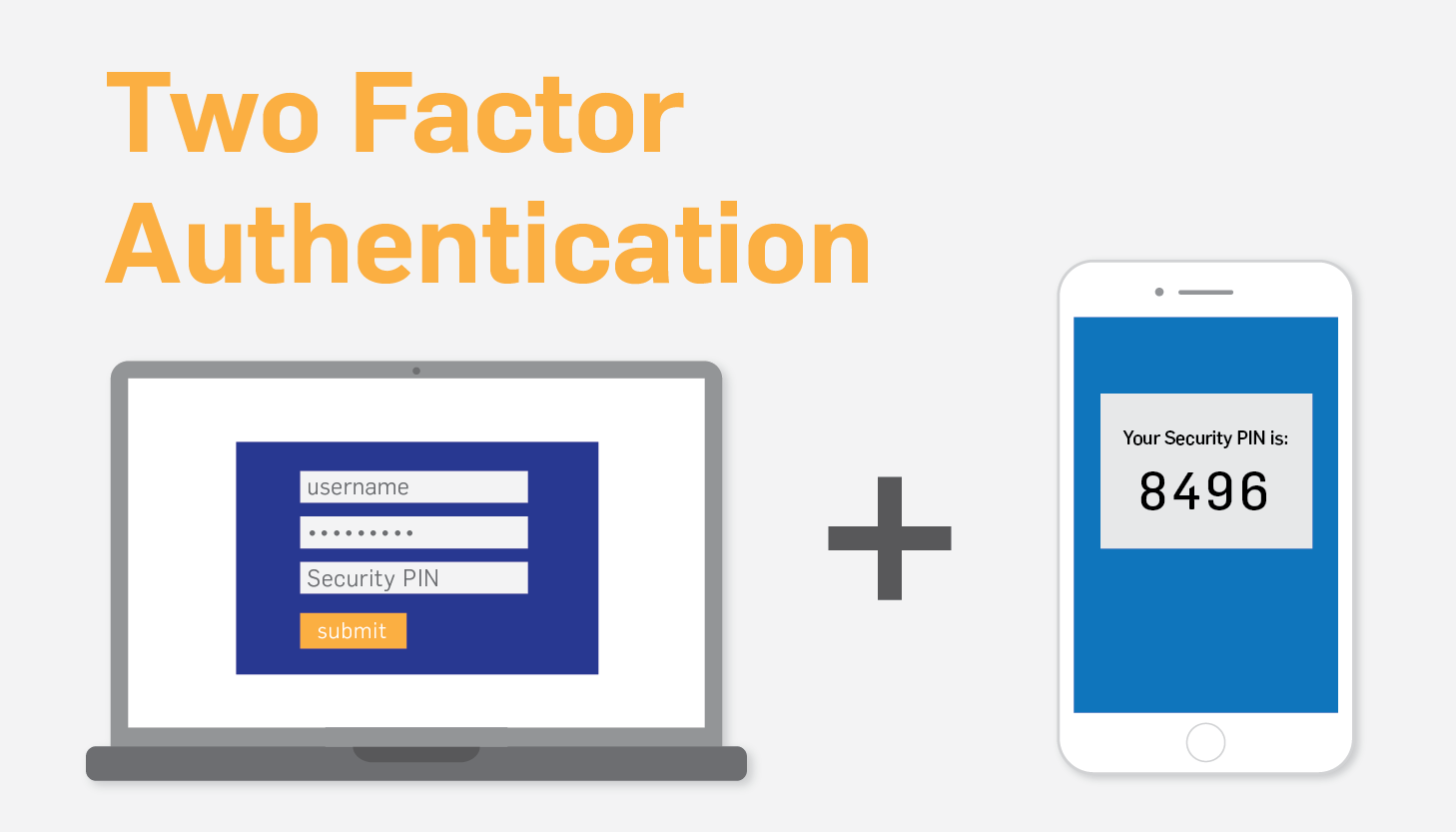
Understanding Two-Factor Authentication (2FA): An Essential Layer of Security
What is Two-Factor Authentication? Two-Factor Authentication (2FA) is a security process that requires users to provide two different authentication factors to verify their identity. These factors typically fall into three categories: By requiring two factors from different categories, 2FA adds an extra layer of security beyond just a password. Even if an attacker manages to […]
Exploring Windows Hosting: Understanding the Pros and Cons
What is windows hosting? Windows hosting refers to web hosting services that utilize servers running on the Windows operating system, typically Windows Server. In Windows hosting environments, websites and web applications are hosted on servers that run Windows Server operating system along with other Microsoft technologies such as ASP.NET, .NET Core, Microsoft SQL Server, and […]
The Importance of URL Masking for Web Security and Privacy
URL masking is a technique where a different URL is displayed in the browser’s address bar than the actual webpage being viewed. It’s achieved by loading the desired webpage’s content within a frame or iframe on a different webpage. The URL shown in the address bar remains that of the parent webpage, masking the true […]
Let’s know about IMAP and POP3 settings in mail and their differences.
Introduction Email communication relies on specific protocols for retrieving messages from a mail server. Two commonly used protocols are IMAP (Internet Message Access Protocol) and POP3 (Post Office Protocol version 3) IMAP and POP3. Understanding the configuration variances between IMAP and POP3 is crucial for efficiently managing emails, catering to diverse user needs, and ensuring […]
What are the causes for mail issue and its solutions in control panel
Introduction: Email has become an indispensable tool for communication, yet encountering issues while using it is a common frustration. Various factors can disrupt the seamless flow of emails, ranging from technical glitches to configuration errors. Understanding the causes behind these problems is crucial for implementing effective solutions and ensuring uninterrupted communication. In this discussion, we’ll […]
How to zip and unzip in Linux with Examples
Description A Zip archive is a compressed file format that supports lossless data compression. A zip archive might contain multiple files and directories inside it. Zip is a very popular archive file format. Almost every operating system supports zip including all the operating systems by Microsoft as well as all the Linux operating systems. In […]
How to disable direct root access in Linux
Description It is very important to secure your Linux server to protect your data, intellectual property, and time from the hands of crackers (hackers). Everybody says that Linux server is secure by default and to some extent this is true. Linux has in-built security model by default. We need to tune it up and customize […]
How to check memory usage on CentOS
Description : Linux operating system comes with many commands to check memory usage. The “free” command usually displays the total amount of free and used physical and swap memory in the system, as well as the buffers used by the kernel. “top” command provides a dynamic real-time view of a running system. The top command can display […]